Prometheus probe
Prometheus probe allows you to run Prometheus queries and match the resulting output against specific conditions. You can define metrics-based SLOs in a declarative way and determine the experiment verdict based on their success. The probe runs the query on a Prometheus server defined by the endpoint and checks whether the output satisfies the specified criteria. The outcome of a PromQL query (that is provided) is used for probe validation.
Prerequisites
To use the Prometheus APM probe, you need:
- A running Prometheus server
- Access to the Prometheus API endpoint from the kubernetes execution plane
- Proper configuration of your application to expose metrics to Prometheus
Interactive Setup Guide
Follow along with this interactive guide to learn how to configure Prometheus probe:
Steps to configure
-
In Resilience probe section under chaos module, click on New Probe button
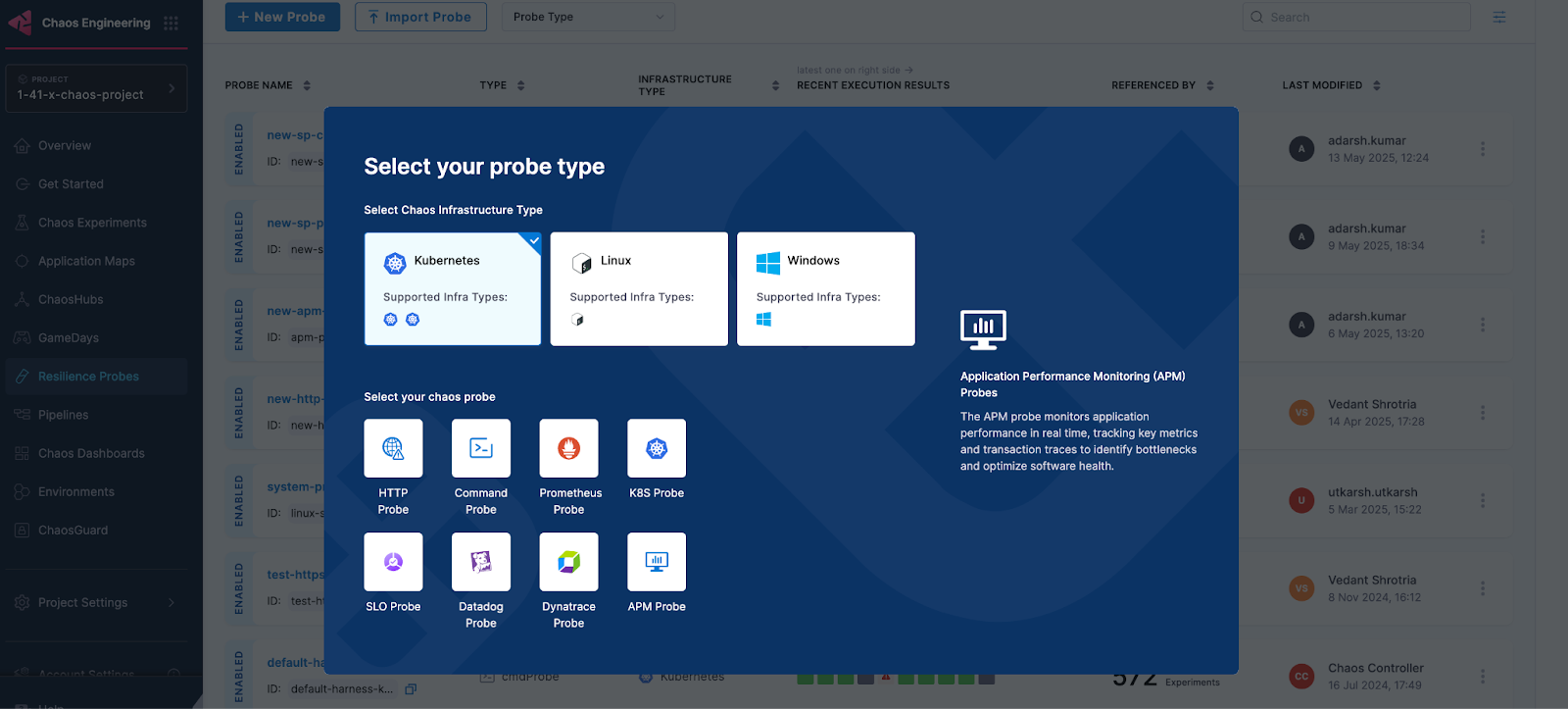
-
Select the APM Probe
-
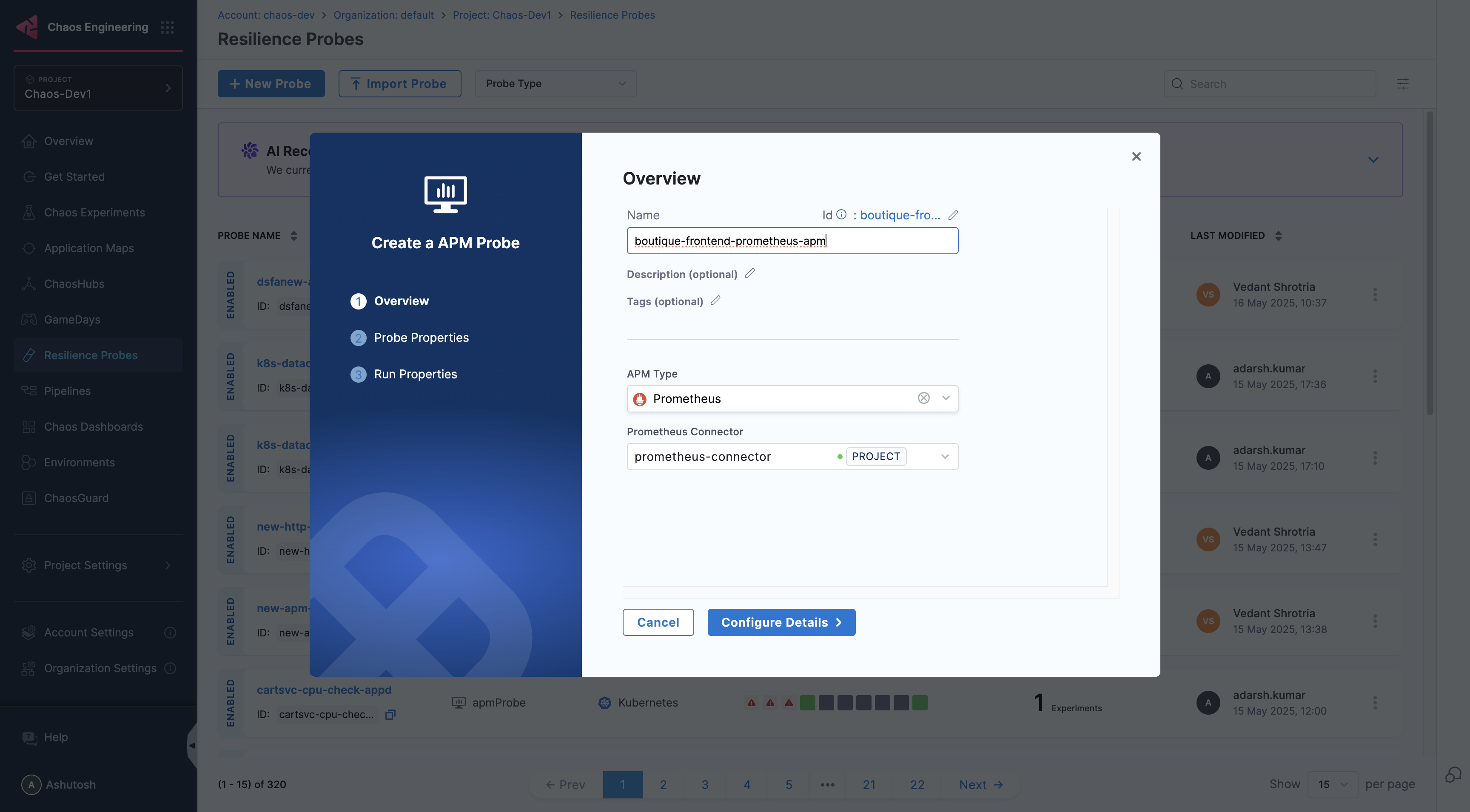
Provide the name of the probe and select Prometheus under APM Type
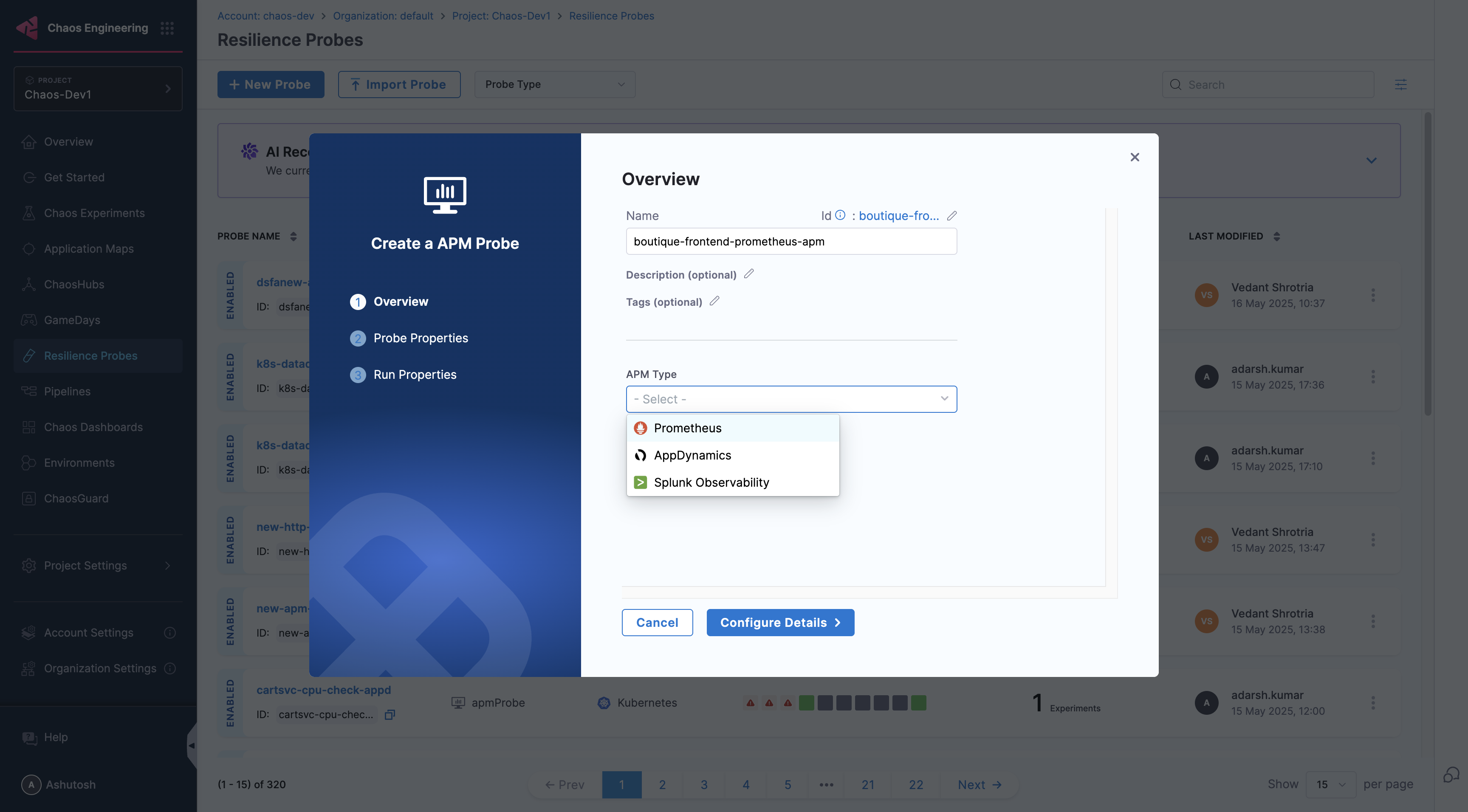
-
Under Prometheus connector select connector
-
In Connector settings, you can either choose an existing connector or click New Connector
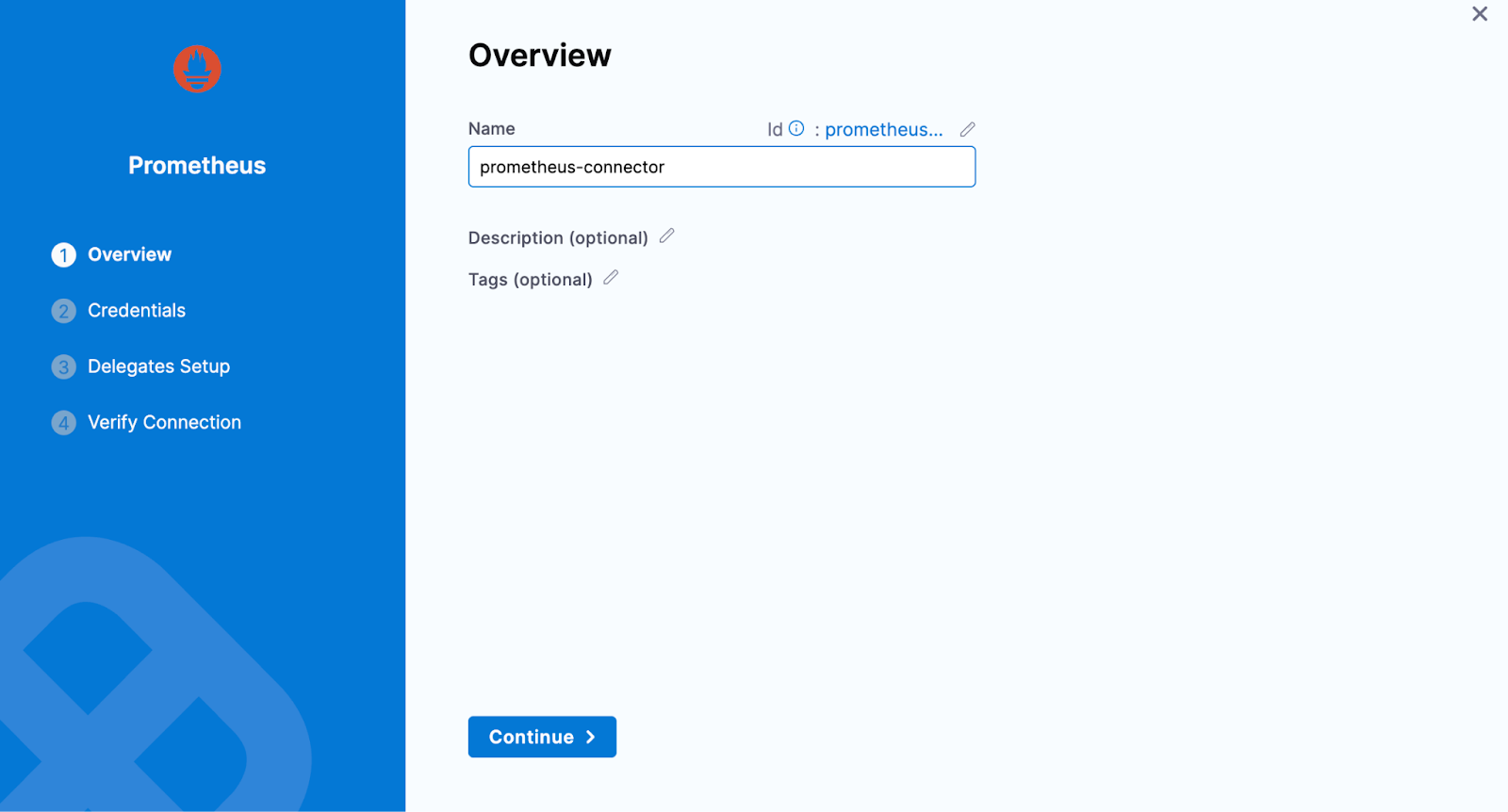
-
Provide the credentials of the Prometheus
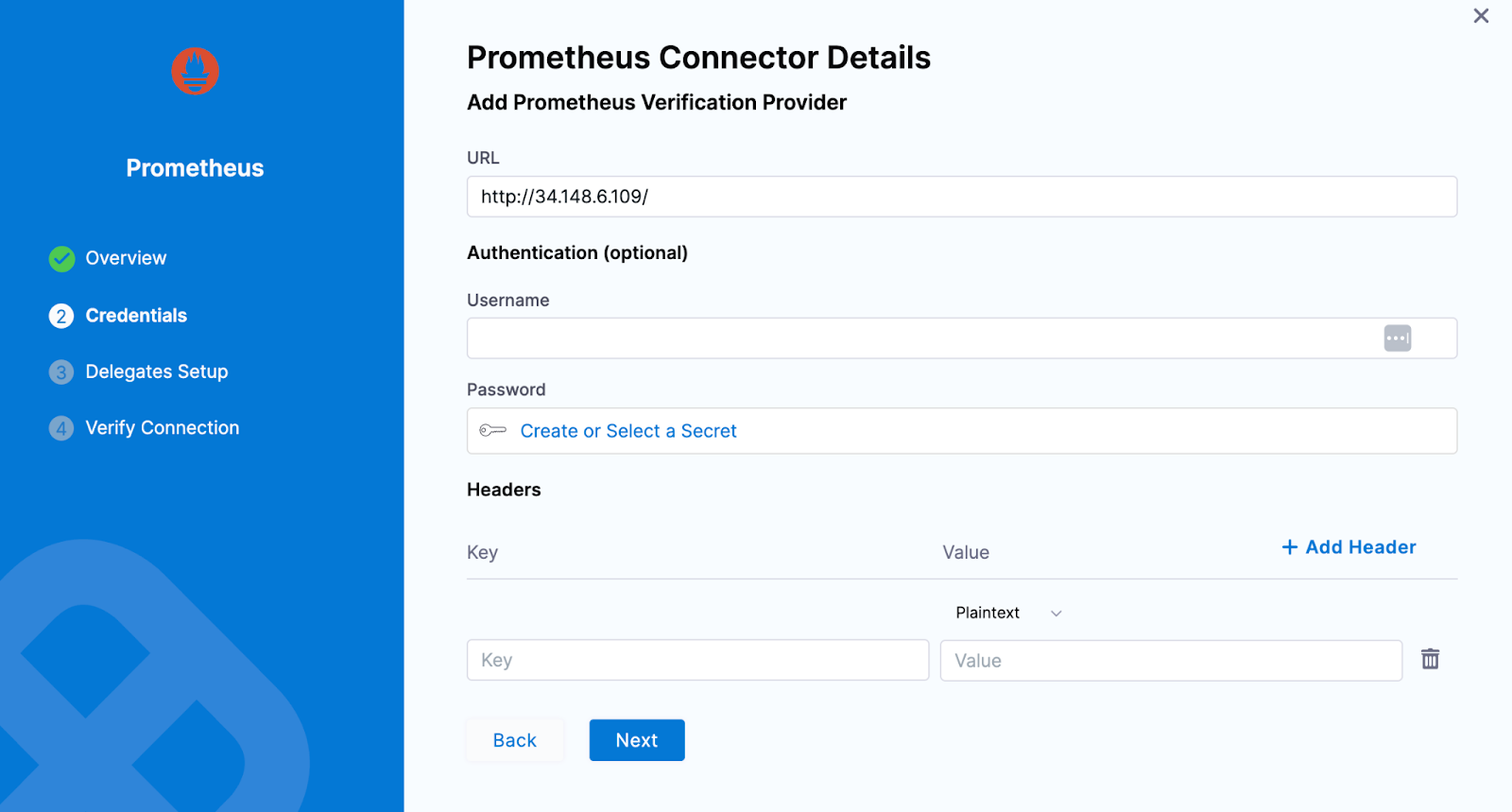
-
Select the delegate and verify the connection and click on Finish

-
Now connector is created and selected, click on Configure Details
-
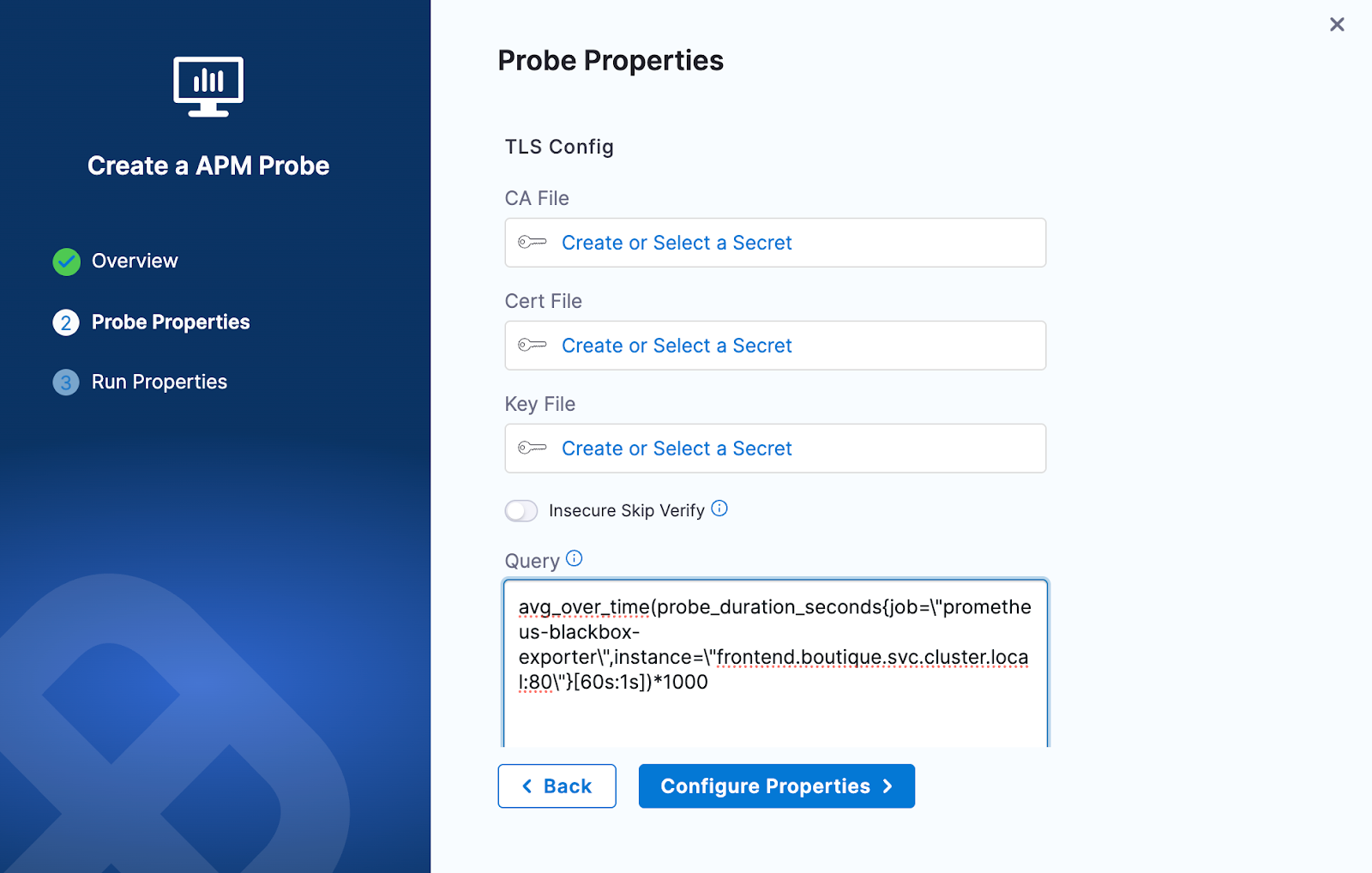
Under Probe Properties pass the value of required parameters
- TLS Config:
- It offers a mechanism to validate TLS certifications for the Prometheus server. You can supply the
cacertor the client certificate and client key to perform the validation. Alternatively, you have the option to enable theinsecureSkipVerifycheck to bypass certificate validation. - For more details, refer to Prometheus TLS configuration documentation.
- CA File: The
caFileholds the file path of the CA certificates utilized for server TLS verification - Cert File: The
certFileholds the file path of the client certificates utilized for TLS verification - Key File: The
keyFileholds the file path of the client key utilized for TLS verification - Insecure Skip Verify: The
insecureSkipVerifysetting skips the TLS certificates checks
- It offers a mechanism to validate TLS certifications for the Prometheus server. You can supply the
- Query:
- The query contains the PromQL query to extract out the desired Prometheus metrics via running it on the given Prometheus endpoint
- Please Note that all the double quotes need to be parsed in the provided query.
- Example:
avg_over_time(probe_duration_seconds{job=\"prometheus-blackbox-exporter\",instance=\"frontend.boutique.svc.cluster.local:80\"}[60s:1s])*1000 - For more details, refer to Prometheus PromQL documentation
- TLS Config:
-
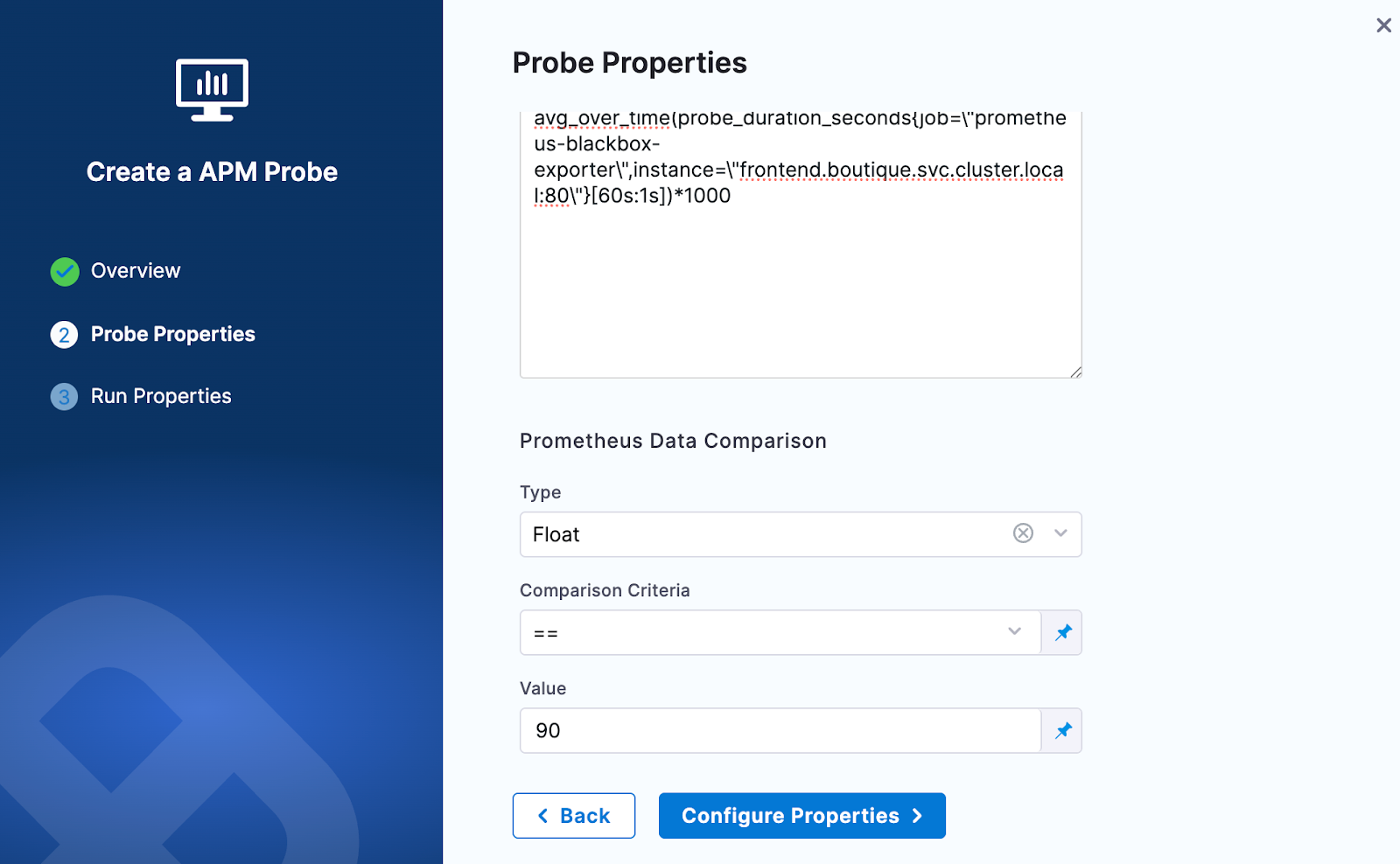
Provide the comparison criteria under Prometheus Data Comparison
-
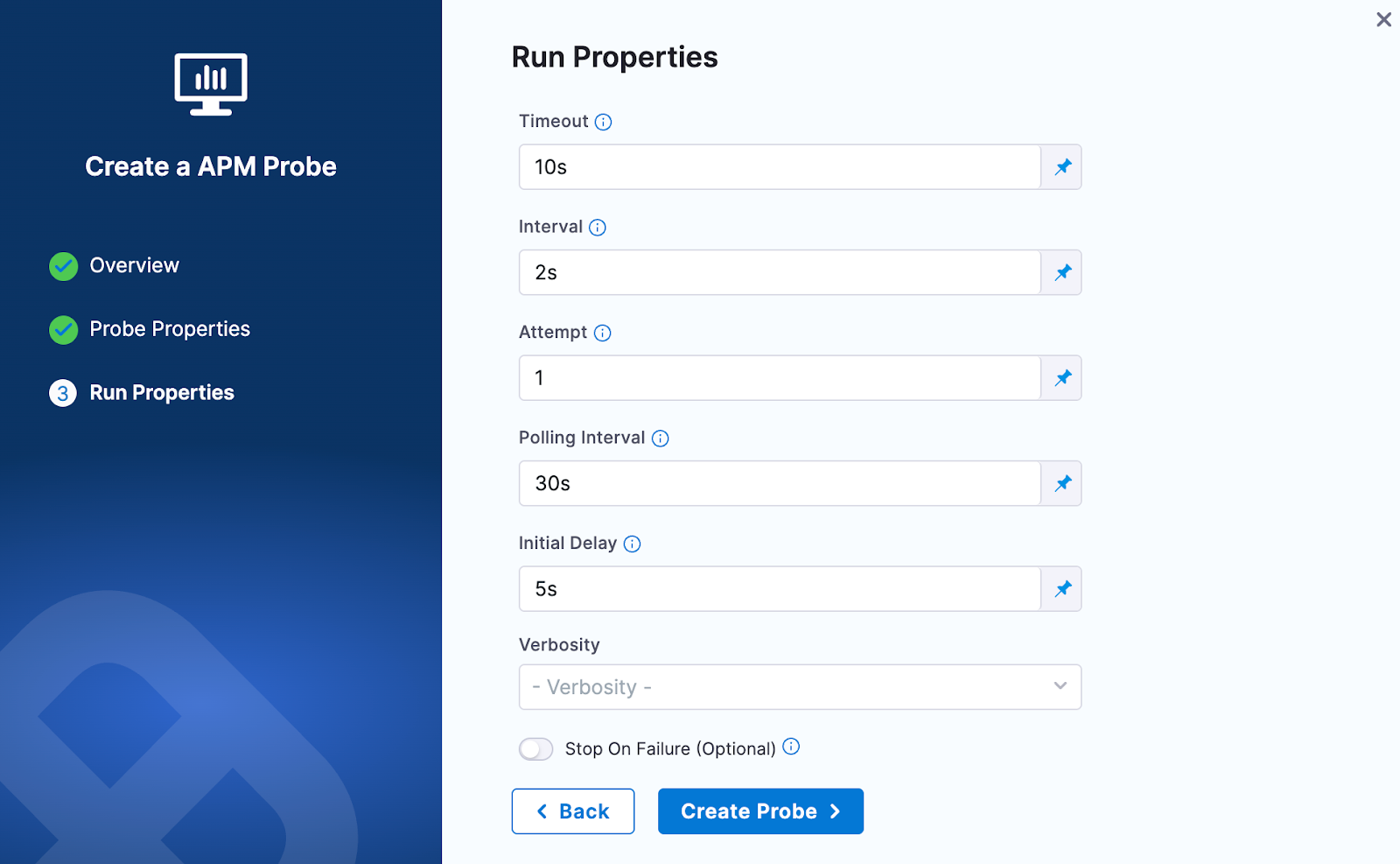
Provide the Run Properties
-
Then click on Create Probe